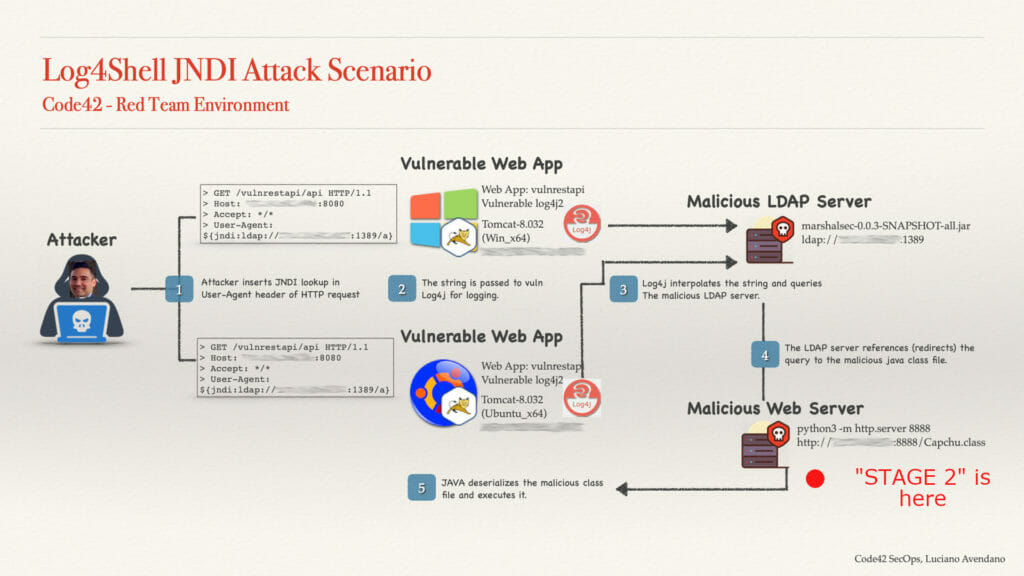
Code42 @ CSO50 2022
The Code42 Security Operations team is thrilled to be attending CSO50 2022 (September 19-21) to accept an award for their project “how to train your incident handling robots”.
how to train your incident handling robots
Code42 is leading the industry in Insider Risk Management (IRM) because we understand that IRM requires an effective Insider Risk Management program as well as an excellent IRM tool, like Code42 Incydr or Incydr Gov. A dedicated program is necessary because IRM investigations are sensitive, and the result can have a serious impact on the career progression of the person involved.
In recognition of the sensitivity of IRM investigations, the Code42 Insider Risk Management team developed an investigation style called Empathetic Investigations™. Read more from Chrysa Freeman in How to Approach Insider Risk Incidents with Empathy on the Code42 product blog.
Good artists borrow, great artists steal.
Pablo Picasso
Just like Picasso, the Code42 Security Operations team learned one way to be great by stealing the concept of Empathetic Investigations™ from our IRM program. Traditional models of Security Operations investigations tend to be a cold and alienating process for people being interrogated about security events. Often context or “evidence” is withheld, leading to individuals answering inquiries in a bubble and feeling they are receiving “guilty until proven innocent” treatment.
In addition to the angst investigations can cause for the person being investigated, it is also a large investment in security team effort to facilitate direct communication with individuals for a wide variety of alerts. It leads to fatigue, stale alerts (e.g. awaiting user responses), and inconsistent perception of the security team due to always working with individuals with different communication styles.
Using the power of chat robots, our SecOps team is building automated workflows that facilitate investigations through direct messages to users from their friendly Slack Security Robot.
So, how are we training our incident handling robots?
Use friendly language and give context for the activity
- Friendly language invites collaboration and demonstrates partnership with you and the security team.
- Example:
“You have triggered a security alert. Please confirm this activity” —> “Hey! It’s your friendly SecOps robot. At 8AM today, your account signed in from a new location in the world. Does this look familiar to you?”
Empower users by enabling them to classify activity
- Responses to Empathetic Investigations™ in Slack are included in calculating whether an alert is benign or should be elevated
- Users know their systems and environments best; this invites them to inform the Security team when unusual activity occurs
Follow up and be clear on next steps
- Follow up with education to provide in-context information about preferred behaviors when behavior was unintended
- Clearly communicate next steps to the user
- Thank respondents for their commitment to protecting themselves and others in your organization
Applied Empathetic Investigations™
The goals of applying Empathetic Investigations™ to security operations are to:
- Improve security culture and inspire folks to see security team positively
- Improve efficiency of security staff through reduced flow of manual follow-up tasks
- Develop user awareness of when they traverse security boundaries and educate on preferred behaviors
Shortly after deploying an early version of these incident handling robots, they demonstrated value by educating an admin that an AWS workflow was applying an access rule they had never noticed before. It’s been a joy to see how this improvement to the security investigation process educates individuals about potentially risky actions that automated workflows perform without their knowledge!

We are grateful to have been selected as a 2022 CSO50 Award Recipient, and we look forward to seeing you next week at MGM National Harbor in Maryland!