How do we contribute back to the Open Source Community?
We have all heard about the term “Open Source”. This refers to the code that is either written by an individual or group of people or community and made available to the public to access for free. The code is available for anyone to view and modify under the open-source license agreement. One such project that is very popular among the cloud governance community is Cloud Custodian from Capital One. In this blog we will discuss what Cloud Custodian does, associated components, and how we use it and contribute back to the community.
What is Cloud Custodian?
Cloud Custodian is Python-based and has many scripts, tools, and capabilities all in one application. It is a rule engine where you can write policy definitions in YAML. This enables an organization to manage their public cloud resources by writing policies for cost savings, exploring asset tagging, compliance, security, operations-related concerns, and resource inventory. Cloud Custodian supports AWS, Azure, and GCP Cloud Providers.
Open Source | Python-based | Agentless | Serverless | Governance-as-Code | Real-Time Guard Rail | Visibility | Powerful Cloud Security Management Tool
The first step is to write the simple YAML DSL policy that allows you to define the rules that include the resource type, filters, mode, and actions. The below command will deploy the Cloud Custodian policy as a Lambda function. custodian run -s . policy.yml –assume arn:aws:iam::123456:role/c7n
Cloud Custodian, behind the scenes, automatically creates the CloudWatch Log Group and CloudWatch Event Rule. Within the policy, you can define the output directory where the Cloud Custodian can save the output. In this case it is an S3 Bucket. It can further be ingested into your SIEM solution where you can write different queries and draw dashboards.

What does a Policy look like?
The example below shows what a Cloud Custodian policy looks like:
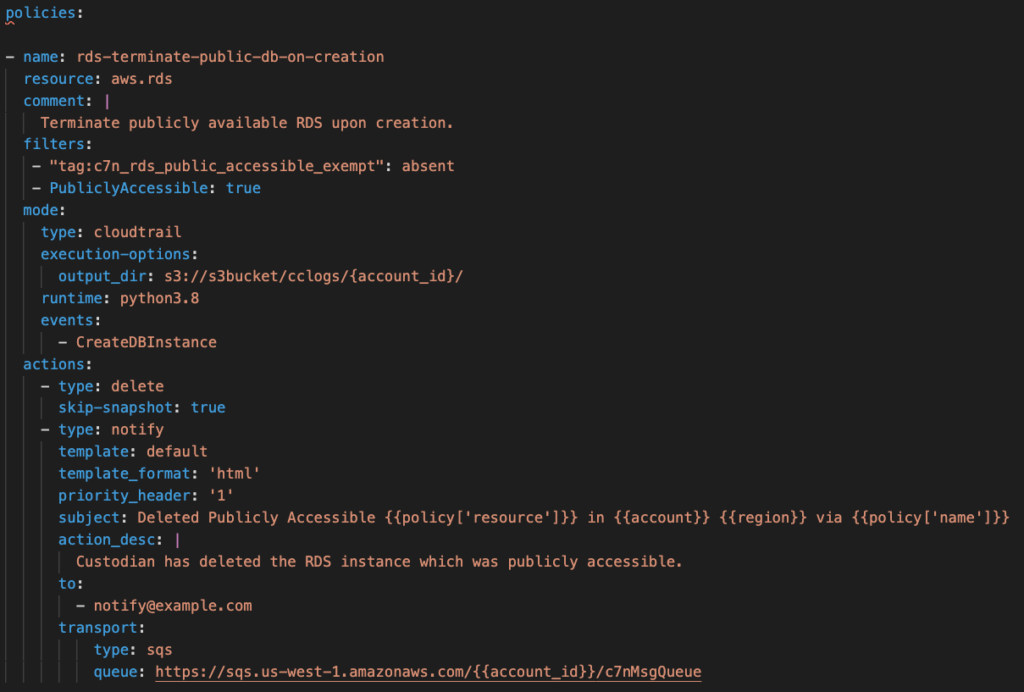
The policy contains the name, resource type, filters, mode, and actions. The above policy applies to the resource type “aws.rds”. Under filters, we have allowed the exemption tag if the business wants the RDS instance to be accessible to the public. Cloud Custodian is looking for a filter named “PubliclyAccessible”. When it finds the value to be true, it flags the resources for non-compliance. The mode type includes the schedule of the policy to run. In this case, it is based on the cloudtrail events. The action defined is to delete the RDS and skip the snapshots. It will also send an email notification to notify@example.com. It will use the default template in HTML format.
How are we giving back to the community?
The Code42 team responsible for Cloud Custodian has been very active and engaged with the community, both leveraging existing knowledge, innovating, and giving back. We share back with the community by engaging in a real-time chat at Gitter, submitting issues at GitHub, writing blogs, and sharing the policies we have created and have had success with. You can find various Cloud Custodian blog posts on Medium that have been created by the Code42 team. Below is a breakdown and summary of the topics we have created that you may find useful.
Stories at Medium: https://ismsguy.medium.com/
Introduction
- What is Cloud Custodian
- Tried replacing the Cloud Custodian with Something else…
- A Watchman for Your Cloud that never sleeps, and it’s free!
- Establishing the Cloud Governance Committee
- Relationship between the Cloud Custodian Lambda Function and the CloudWatch Event Rule
Policies for AWS
- Cloud Custodian Policies for CIS AWS Foundations Benchmark (Part 1)
- Cloud Custodian Policies for CIS AWS Foundations Benchmark (Part-2)
- Cloud Custodian Policies for CIS AWS Foundations Benchmark (Part-3)
- Cloud Custodian Policies for CIS AWS Foundations Benchmark (Part-4)
- Propagating Tags from provider level down to all resources using Terraform Template
- Treating the Mishmash of Missing Tag Resources in AWS using the Cloud Custodian (Part 1)
- Identify AWS Resources Exposed to the World using Cloud Custodian
- Identify Unencrypted AWS Resources using Cloud Custodian
- Auto-remediation for missing tags in AWS using Cloud Custodian — Part 1
- Auto-remediation for missing tags in AWS using Cloud Custodian — Part 2
- Auto-remediation for missing tags in AWS using Cloud Custodian — Part 3
Policies for Azure